During today's digital age, the internet can often feel like a wild west where dangers lurk around every corner. Regardless of whether it's identity theft, data breaches, or unwanted surveillance, safeguarding our online presence has always been more critical. One effective tool in navigating this risky landscape is the proxy server. With their ability to act as intermediaries between users and the internet, proxy servers offer a significant layer of privacy, security, and anonymity that can greatly enhance our browsing experience.
As technology evolves, so do methods we use to protect ourselves. Proxy servers serve a variety of purposes, from bypassing geographical restrictions on content to providing an added barrier against potential cyber threats. Understanding what a proxy server is and how it functions can empower users to make wise decisions about their online activities. In this article, we will explore the significance of proxy servers, their different types, the advantages they offer for privacy and security, and how they can be utilized effectively in both personal and professional contexts.
Comprehending Proxy Servers for Networking
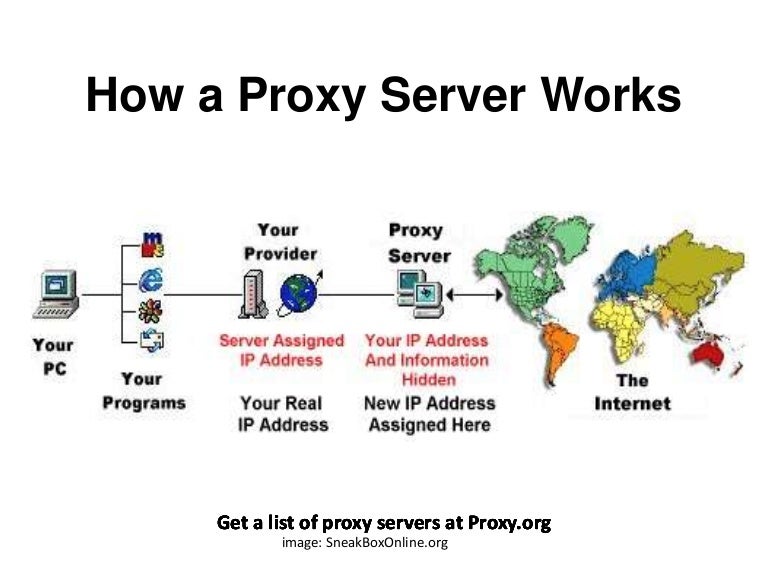
A proxy server acts as an intermediary between a client's device and the world wide web. When you join to a middleman server, your requests for services are forwarded through the proxy instead of immediately to the final server. This implies that the proxy server fetches the data for you, which then enables for various features such as concealment, security, and content filtering.
One of the key functions of a middleman is to supply a level of protection for your online activities. By concealing your internet protocol address, it makes it more difficult for websites and would-be hackers to track your internet activity. This extra layer of anonymity helps protect your identity, making it a important tool for those focused about confidentiality in an ever more interconnected digital world.
Additionally, proxy servers can enhance the general user interaction by enhancing internet speeds and permitting access to location-based content. Different types of proxy servers, such as HTTP-based, Socket Secure, and non-intrusive proxies, cater to different needs, supplying adaptability for users to choose the most fitting option based on their distinct requirements, whether for personal browsing or professional needs.
Benefits and Risks of Proxy Usage
Using a proxy server provides a plethora of benefits, notably in enhancing online privacy and security. By functioning as an intermediary between the user and the internet, proxies can hide the user's real IP address, causing it harder for websites and malicious actors to track online activities. This anonymity can be vital for individuals looking to protect personal information or for businesses that strive to ensure their operations are protected from potential cyber threats. Additionally, proxy servers can help users access geo-restricted content, allowing for a broader browsing experience.
However, there are notable risks connected with using proxy servers, particularly free ones. Free proxies may not have robust security measures in place, putting users to data breaches and malware. Furthermore, many free services track user activities, potentially undermining privacy rather than strengthening it. It's essential to analyze the reputation and trustworthiness of a proxy service to mitigate these risks. Neglecting to do so could lead to exposing sensitive information to third parties.
In the context of business operations, while proxy servers can greatly enhance cybersecurity and productivity, organizations must weigh these advantages against the potential for misconfiguration or inadequate protection. A inadequately managed proxy can lead to security vulnerabilities, potentially exposing the company to harmful attacks. As with any technological solution, it is imperative to invest in reputable proxy services and to adopt best practices for security.
Proxy Services in Various Applications
Companies often rely on proxies as crucial tools for enhancing cybersecurity. By routing internet traffic through a proxy, companies can oversee and sift through outgoing and incoming data. omeka.net/ permits them to prevent malicious websites, prevent data breaches, and ensure compliance with business regulations. Additionally, proxies can deliver anonymity for employees, making it more difficult for external actors to observe their online activities, thus increasing the overall security of the company.
In video gaming, proxies are used to lessen lag and enhance connection stability. Video game enthusiasts often encounter issues like high ping and connection disruptions, which can considerably affect gameplay. By using a proxy server specifically designed for online play, players can experience a more stable experience, avoid regional restrictions, and even enhance their chances of not getting suspended for IP misuses. This ensures a smoother gaming experience and better access to game servers worldwide.
Proxies play a vital role in web scraping and data collection for business analysis. Analysts and companies use proxies to collect data from websites without raising alarms or being blocked. Various kinds of proxies, such as private and data center proxies, facilitate users to retrieve information seamlessly while staying anonymous. By using proxies, businesses can remain competitive of competitors, glean insights from market trends, and adjust their strategies as needed without facing the dangers associated with direct scraping attempts.
